How Key Users Drive Success for Digital Transformation
In the realm of digital transformation, one driving force stands out: Key Users. These individuals aren't just stakeholders; they're the engines of change within your organization. With a profound understanding of new processes and systems, Key Users are the go-to experts for navigating the new landscape and guide their peers through transformation. As exemplified by various studies, active user involvement brings substantial benefits, such as up to 60% higher project success rates (Gartner 2012), faster completion (Standish Group 2015 CHAOS Report) and lower cost (McKinsey & Company 2011). This is why the right selection, onboarding and engagement of Key Users can be a game-changer for a high Return on Investment (ROI) of your project.

How Key Users Drive Adoption and ROI
Key users – in some organizations they are also named power users or super users - perform user acceptance testing of technology and processes and deliver end user training. After the transition to the new business solution, they continue to serve as key contact and trainer for new users and solution changes. In the period immediately after a technical go-live, they will also serve as a link between the organization and the support team to log tickets and follow-up on any issues.
With these tasks, Key Users are the closest contact to many end users such as their peers, line managers and process owner which enables their role of change agent. In their interactions with their colleagues, they strongly influence the perception of the digital changes in the organization, help employees to embrace the new ways of working, to execute the processes as designed and use the system as intended.
In other words, the speed of adoption, the usage of the system and therefore ultimately the ROI of your project relies heavily on the way your Key Users interact with the organization.
Let’s look at the different ways, how knowledgeable and engaged Key Users will drive project results and benefits:
- Detecting inconsistencies early:
While learning the new ways of working and testing new technology, the Key User will detect inconsistencies or interdependencies with other functions that can be resolved at an early stage. - Identifying feasibility of key business scenarios:
At the formal User Acceptance Testing (UAT), you can rely on your Key User to detect important glitches to be fixed as he or she knows about the key business operations and future processes. They can also point out any less obvious, but relevant scenarios that need to be tested. - Reducing Resistance and Anxiety about the Changes:
Even before the official end user training, engaged Key Users will talk to their colleagues about the new ways of working and update them on key changes in a way that reduces anxiety and gives their fellow co-workers confidence in the new solution. - Ensuring training content is fit for colleagues:
For the End User Training, the Key User will prepare (or help to prepare) the right level of materials which their co-workers will need to learn the new ways of working. Knowing the level of expertise of their colleagues and the major process changes of their area, they will adapt the training to be effective. - Guiding colleagues on the new solution:
After transition, the Key User will work closely with the colleagues who use the new process for the first time and notice any needs for coaching or retraining. - Link between business and IT:
It is also the responsibility of Key Users to log all glitches, process issues and system errors for correction. As an experienced employee, they will be able to differentiate the criticality of problems for correct prioritization. - Continuous improvement of new solution:
Back to business as usual, it is often the Key Users who discover additionally required system functionality or suggest process and system improvements. With their deep knowledge and being embedded in the business processes, they thoroughly leverage the new digital solution and drive continuous improvement.
Therefore, the ultimate usage and materializing benefits of the new solution is highly dependent on the communication skills and engaged work of the Key Users.
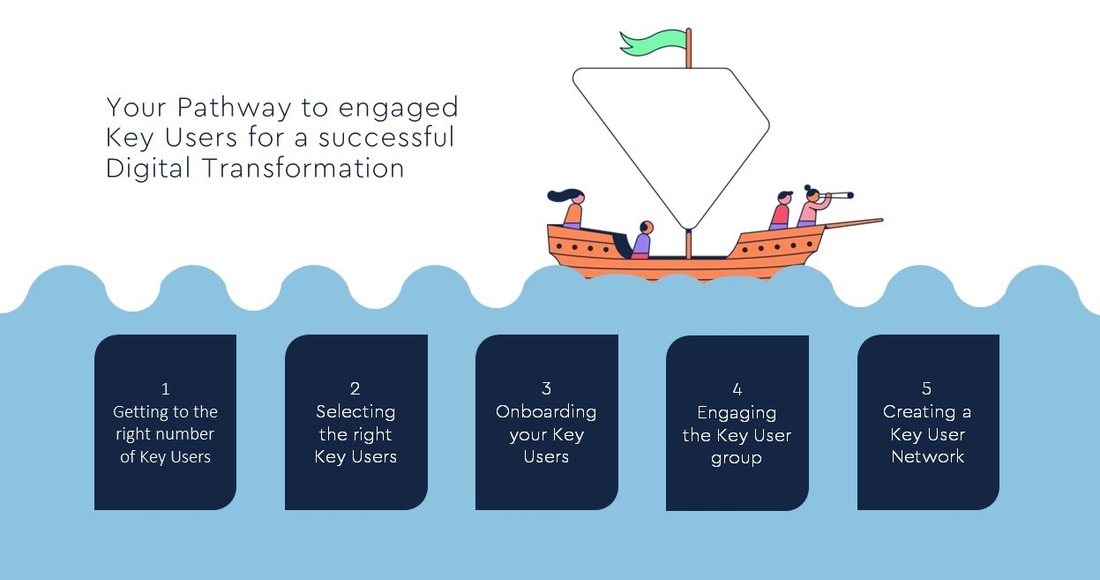
How to Select and Engage Key Users
Since the positive impact of engaged Key Users is significant, the question is: how do we get there? Let’s look at the most important elements of engaging Key Users:
- Getting to the right number of Key Users:
The number of End Users per Key User differs with the complexity of the system (number of functions) and the level of support you expect your organization will require. As you want all users to have easy access to their Key User, you should consider the number of countries or plant sites and languages that need to be supported.
One Key User per function and site is a good starting point for planning but needs to be adjusted if the number of End Users is large. Especially when dealing with a transformative change that needs close support, it is our recommendation that the ratio of End Users per Key User does not exceed 20/1. Please keep in mind that the Key User role can only be carried out effectively in a setting that allows sufficient time for personal interactions.
As the biggest concern from the key users’ line managers is usually the amount of time required for project tasks, transparency of expectations and alignment with the function who nominates a key user is important. - Selecting the right Key User:
Given the importance of their role, Key Users should be respected employees with a deep level of process knowledge. Especially for small enterprises, it can be a challenge to take a resource from daily operations. However, it turns out that it is worth the effort to send those employees with solid experience in your company and profound knowledge on business operations to the project. You may consider reassigning some of the duties to other team members or hiring additional temporary help. Most importantly: do not take the person that can be spared just because it is challenging to free up your high performers! - Onboarding of your Key Users:
In the onboarding process, it is important to clearly communicate the WHY of the project and clearly link it to the company’s strategy. Even though the Key Users might have heard some project communication before, linking the reason for the change to their new role as Key Users makes a difference on how they view their own role and in the way they communicate to their peers. Ideally, we want the Key Users to be proud of being part of the initiative and to support the overall strategy.
A personal address of the project sponsor or another senior executive, for example within a key user kick-off event, should be part of the onboarding to stress the importance of the transformation before explaining in detail their role and responsibility in leading and promoting change in the project and beyond. - Engaging the Key User group:
Regular invites of the Key User group are important to prepare them for upcoming tasks and phases. Especially the formal testing, training material creation and hyper-care processes are tasks that require an in-depth communication and preparation beyond the technical content. In those sessions, the Key Users are introduced to project specific lingo, new terminology and receive updates on project specific topics. It is a safe environment to ask questions and bring up any issue. The regular Key User sessions are also important touch points for the project team to receive feedback. With a short questionnaire, we can assess the readiness and the Key Users can voice any areas of concern. It is important to review the results and take appropriate action. The Key Users will be supported in various ways by the OCM and communications team by providing templates and communication aids and they can rely on the functional support by the consultants and their Business Process Lead.
In case the project encompasses training material creation and training delivery, the Key Users are being equipped in a specific train-the-trainer workshop with the basics of adult learning principles, e.g. how to engage learners and assess effectiveness. - Creating a stable Key User Network:
After successful go-live and giving close support during the hyper-care phase, the group of Key Users will keep their responsibilities while moving back into their business role. You want your specialists to stay engaged to onboard new employees, reinforce the utilization of the new technology and test any system changes.
Conclusion
The Key User role is essential for any major digital change initiative and has the potential to make or break it. If life sciences companies want to transform into technology-centric organizations, they should systematically utilize this role and not only leave it up to individual program or project managers to decide whether and how to deploy key Users. Our experience shows that the strategic and consistent deployment of Key Users improves the digital transformation capability and significantly increases the chances of success. In the end, it’s not just about a successful program, but about enhancing the company’s ability to transform and consistently drive strategic change.
Careful selection, diligent onboarding and engagement of Key Users is therefore imperative for a high Return on Investment (ROI).
Do you have questions about how to strategically plan and set up a change agent and key User network? Please reach out to our OCM experts, Gudrun Maul and Yvonne Kirner. We are happy to support you in your digital transformation.
Stay up to date with the latest #Lifeattenthpin #LifeSciences #Pharma #MedDevices #Biotech #Digitalforlife #Thoughtleadership #Medical Technology #AnimalHealth news by following us on Instagram #LifeAtTenthpin Facebook Tenthpin and our Tenthpin LinkedIn corporate page.

